Malicious hacker Answer 1. Which of the following best describes the order of occurrence of the infection cycle.
Introduction To Ipc Infection Prevention And Control
Type I authentication something you know.
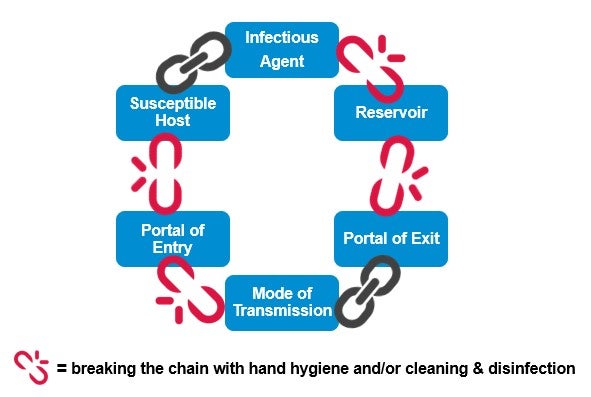
. These practices apply to which of the following. Which of the following best describes a susceptible host. Group of answer choices The method by which a pathogen is transmitted A description of the susceptible host A process for killing pathogens The way a pathogen is treated once it enters the body.
Which of the following molecules represent the primary or prototypical members involved in signal 2 mediated activation of naïve T cells. Susceptible hosts differ from the general population because they are far more likely to. Choose one best answer Agent host environment.
By contrast an immune person is one who has a high degree of resistance to the organism and who when exposed does not develop the disease. Which of the following sets of words best completes the following sentence. A susceptible host is a member of a species population who is at risk of becoming infected with a certain disease due to a variety of reasons.
Which of the following best explains how devices and information can be susceptible to unauthorized access if weak passwords are used. And are a portal of exit. CD28 B7-1 or B7-2.
Which of the following statements best describes a white-hat hacker. In ___ offspring. Typhus Lyme disease and Rocky Mountain spotted fever are from the family.
In this model the disease results from the interaction between the agent and the susceptible host in an environment that supports the transmission of the agent from a source to that host. C Chance can play a big part in peoples fates. Which term describes aristotles opinion on knowing the different types of government.
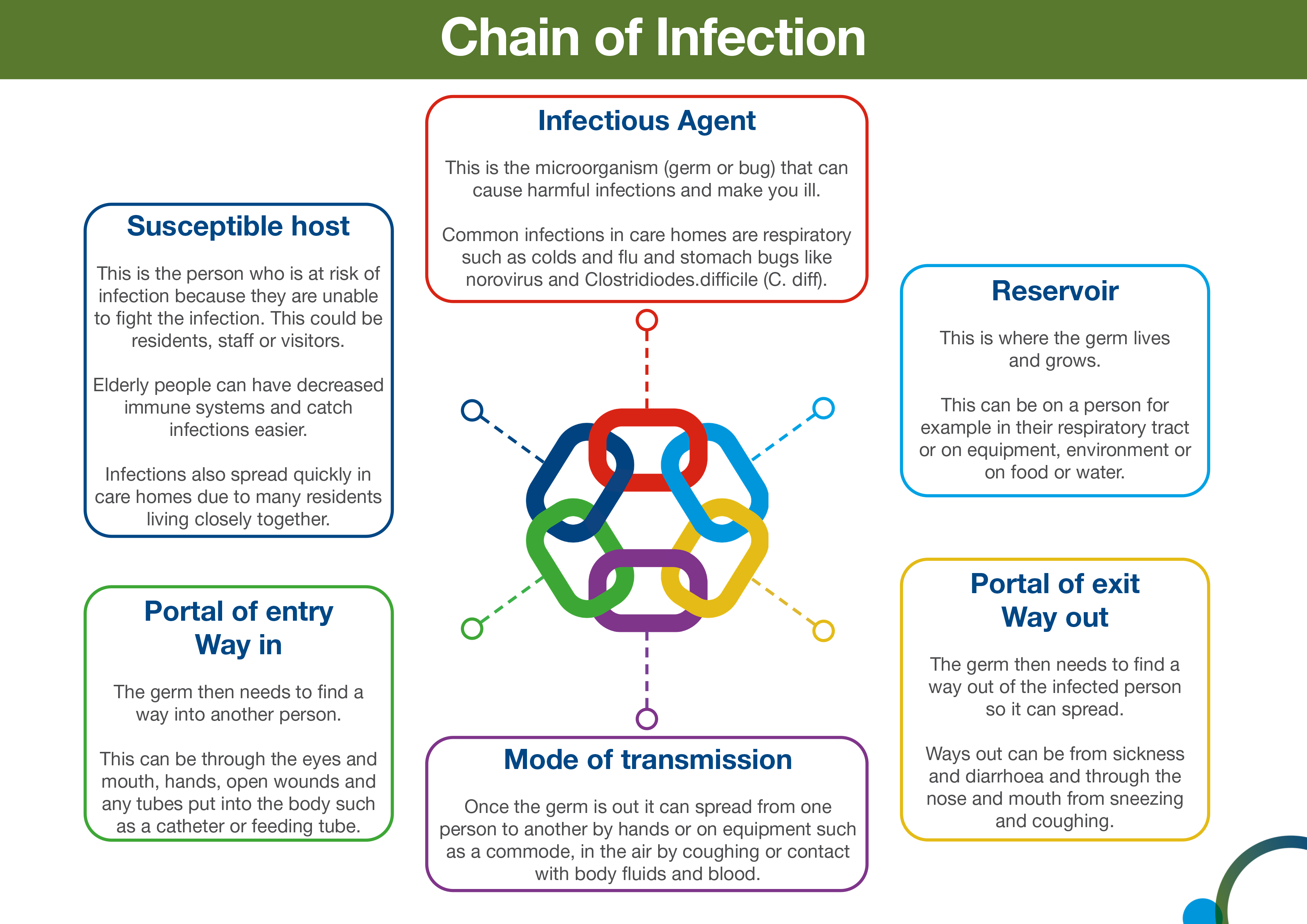
Simply another term for SSO. B Unauthorized individuals can exploit vulnerabilities in compression algorithms to determine a. More susceptible to disease including age young people and elderly people generally are more at risk underlying chronic diseases such as diabetes or asthma conditions that weaken the immune system like HIV certain types of medications invasive devices like feeding tubes and malnutrition.
1043 students attemted this question. The epidemiologic triad of disease causation refers to. John Snow Robert Koch Kenneth Rothman.
CTLA-4 B7-1 or B7-2. Source mode of transmission susceptible host. A The human heart is difficult to predict B Tough decisions bring out the worst in people.
B Students teenagers especially always desire the approval of their peers whether consciously or unconsciously. Other host factors known to be associated with increased susceptibility to infection include dead or poorly perfused tissue in burns and wounds loss of mucosal barrier function such as occurs in the tracheobronchial tree of mechanically ventilated patients and disruption of the normal bacterial flora in the gastrointestinal tract and oropharynx. 1 Susceptible host 2 Portal of exit 3 Infectious agent 4 Reservoir host 5 Means of transmission 6 Portal at entry a 123456 b 234561 c 342561 d 432651.
It is restricted to use within a specific domain or area of the network. For each of the following identify the appropriate letter from the time line in Figure 127 representing the natural history of. Which of the following best describes how to inhibit bacterial growth.
According to the CDC standard precautions should be practiced at all times. A Students are susceptible to all sorts of outside influences. This preview shows page 1 - 2 out of 4 pages.
Ensuring safety in the workplace. It is portable and can be used across business boundaries. The triad consists of an external agent a susceptible host and an environment that brings the host and agent together.
A white-hat hacker is a good guy who uses his skills for defensive purposes. E Agood relationship requires putting faith in the those we lokhy. For an infection to develop each link of the chain.
SUSCEPTIBLE PERSON HOST A susceptible or non-immune person is one who has little resistance against a particular organism and who if exposed to this organism is likely to contract disease. A security audit performed on the internal network. Which of the following best describes a federated identity.
MA 10110 Final Study Guide 1. For each of the following risk factors and health outcomes identify whether they are necessary causes sufficient causes or component causes. The following best describes TCR recognition of antigen.
Which TWO of the following best describe the major themes of the short story. The and the are the best type of susceptible host. Binds to conformational determinants of whole.
Read the Anthrax Fact Sheet on the following 2 pages then answer the questions below. Which of the following best describes the order of occurrence of the infection cycle. Which of the following best describes a central idea of the text.
Former grey hat D. Which of the following best describes the primary purpose of OSHA regulations. The problem with early straw polls is that they didnt have one of the following characteristics.
D Civilized justice does not mix well with barbarism. Describe its causation in terms of agent host and environment. Which areas of the world are most susceptible to desertification.
Unauthorized individuals can deny service to a computing system by overwhelming the system with login attempts. Former black hat C. C The pressure to conform or be popular with ones peers may negatively.
Which of the following best describes a susceptible host. Which of the following describes mode of transmission.

Covid 19 The Chain Of Infection Transition From Hospital To Home Cloroxpro

0 Comments